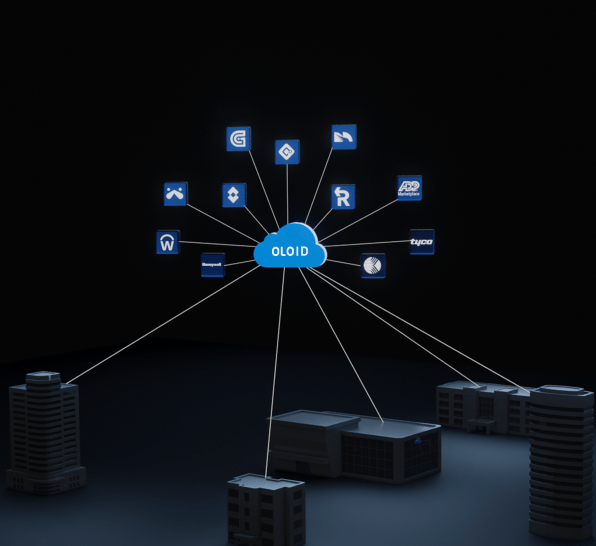
RFID cards, or Radio-Frequency Identification cards, are used for tracking and identifying objects wirelessly. They consist of a small chip and antenna embedded in a plastic card, similar in size...
Subscribe to our Blog
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et.
[gravityform id="13" title="false" description="false" ajax="true" ]